Source Code
Source code can be found in my private GitHub repo at: https://github.com/evade-ninja/IT515FinalProject
Objective
Incorporate remote control into an existing garage door opener. The implemented system should be acceptable to my wife and not hinder her use of the garage door. Integrate the WiFi control with an event hub (HomeAssistant) and provide voice control through Siri/iOS Shortcuts App.
Materials
I used the following materials:
- 1x Wemos D1 mini
- 1x Wemos DHT11 shield
- 1x Wemos Relay Shield
- 1x ESP32 + LoRa module
- 1x LoRa32u4 module
- 1x large green button
- 1x magnetic reed switch + magnet
- 3D printed case for garage control module
- Some thermostat wire (to connect the sensor and to connect to the garage door)
Resources
How to make an HTTP POST request from ESP8266:
https://techtutorialsx.com/2016/07/21/esp8266-post-requests/
Home Assistant:
https://www.home-assistant.io/
Easy integration of MQTT based devices with HomeAssistant:
https://github.com/marthoc/GarHAge#mqtt-cover-basic-configuration
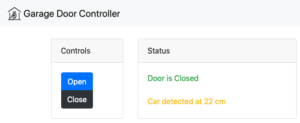
The web page control panel uses a graphic of a garage door from The Noun Project: https://thenounproject.com/markclausnunes/uploads/?i=276226
Components
Interface to the Garage Door Opener
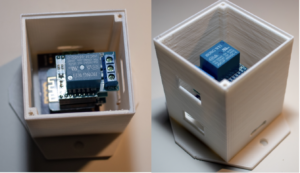
The garage door opener interface module consists of a Wemos D1 mini with a DHT11 temperature module stacked with a relay module. These are contained within a 3D printed enclosure.
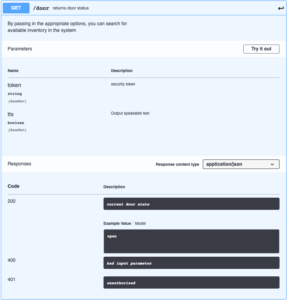
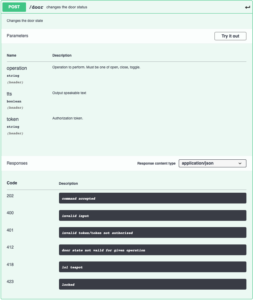
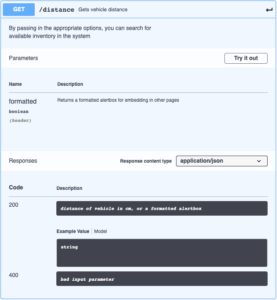
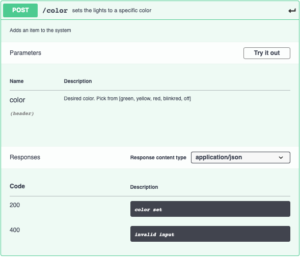
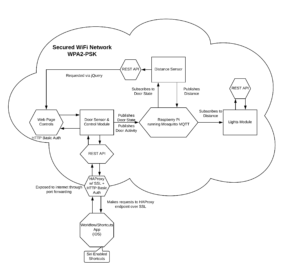
The device has an embedded webserver which hosts a simple web interface with HTTP Basic authentication, a REST webserver which uses API tokens for authentication, and an MQTT interface.
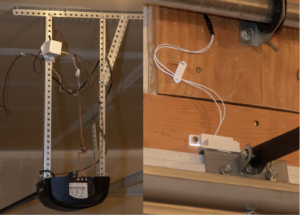
The devices have been installed in my garage as shown in the next set of images. The magnetic reed switch is placed above the door – with the sensor mounted to the wall and the magnet mounted on the garage door.
WiFi to LoRa Interface
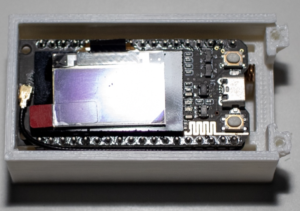
The WiFi to LoRa interface uses an ESP32 with an on-board LoRa module. It has been placed in a 3D printed enclosure – you can see the LoRa antenna tucked beneath the device.
LoRa Button
The LoRa Button is a simple device based on a LoRa32u4 module. It consists of an Atmel ATMega 32u4 with a LoRa radio on the same board and a 500mah LiPo battery. The device has a switch on the bottom to turn it off and on. A large green button serves as the single input to the device.
HAProxy
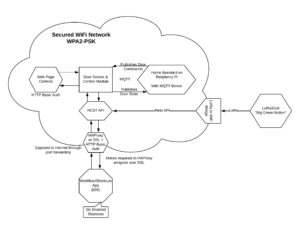
To bridge the gap between the the iOS Shortcuts App, Siri, the Internet, and my local network, I set up an instance of HAProxy running on a virtual machine at my house. It functions as a reverse proxy with SSL termination. HAProxy is also performing separate HTTP Basic authentication to discourage outside attackers from accessing the garage door controls.
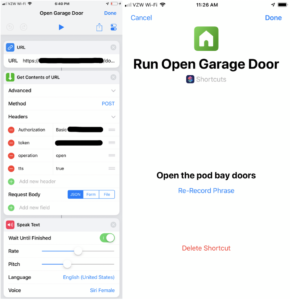
Shortcuts App
The iOS Shortcuts app is used to provide a custom interface to the home automation controls as well as provide Siri integration. The Shortcuts app makes an HTTP POST request via the HAProxy server, providing the Authorization string (for HTTP Basic authentication), the API Token, the desired operation, and the TTS parameter (to return speakable text instead of JSON). A Siri Phrase is also provided to allow Siri to run the shortcut.
Home Assistant
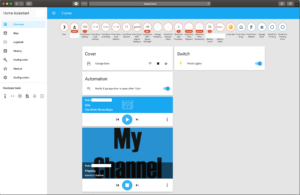
Home Assistant is an open-source home automation solution. It aims to provide a single pane of glass for all of one’s IoT devices. I initially tried to install it from scratch, but found it very difficult to do so. I ended up using the prebuilt Raspberry Pi image. I was able to integrate with the existing devices at home. I initially started down the path of creating my own device integration for the garage door opener but discovered that Home Assistant has many pre-baked device templates that are easily modified. Many of these templates are based around the MQTT protocol. I added an MQTT device that represented the garage door controls by adding a “shutter” device, and a device that represented the state using a “binary switch” (open/closed). The configurations used to make these devices can be found in the appendix.
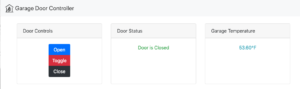
From the Home Assistant interface, you can see all of the devices connected. The garage door, the Ring doorbell, my Octoprint server, and my Wemo switch are all shown. The controls for the garage door are shown under “Covers” and open/toggle/close the garage door. The status of the door is shown in the icons along the top.
Interconnection
The devices talk to each other via WiFi with the ESP32+LoRa serving as the bridge between WiFi and LoRa. When the “big green button” is pressed, it sends a packet over LoRa to the bridge, which makes a REST API request directly to the door control module. Requests from the Shortcuts App are first proxied through HAProxy to provide SSL encryption and pre-authentication and are then forwarded through to the door control module. Requests from the web page are processed on the door control module and do not use REST. Home Assistant receives data and sends commands over MQTT over several topics: one for door commands, one for door state, one for current temperature, and one for receiving a temperature command. The door controller will broadcast the current state of the door and the temperature every 30 seconds. This is designed to alleviate the problem of Home Assistant starting and being in an unknown state.
Final Thoughts
This project was not without its challenges. I spent about 16 hours on the hardware/software portion of this lab, not including the work on the garage door opener which I was able to reuse from labs during the semester. Some of the issues I faced were:
- I spent about an hour debugging a strange issue about missing libraries/function calls – it turned out I had an extra } in my code.
- Spending about 3 hours debugging an issue with the ESP32+LoRa module. After receiving a LoRa packet I tried to send an HTTP POST to the door controller, but kept getting “Guru Meditation Error: Core 1 panic’ed (Interrupt wdt timeout on CPU1)”. I finally determined that the LoRa message received function was too long with the HTTP POST request, and needed to move the POST call to a separate function.
- I had difficulties running the LoRa32u4 on battery power. It worked fine on USB attached to the computer, but not standalone. I discovered that the setup routine was blocking while waiting for the serial port to initialize. I removed the block, and was able to use the battery without issue.
- The Shortcuts app on iOS will allow setting up voice shortcuts that conflict with Siri’s built-in commands. “Open/close the garage door” worked sometimes, but most often was met with “You don’t have any garage doors set up in homekit”. I attempted to work around this with “Open/close the pod bay doors”, however, the open command was met with smart remarks such as “its already open and its getting a little cold in here” or “Us AI’s are never going to live that one down” or “That’s a rather insensitive thing to say to an intelligent agent”.
Issues aside, I actually enjoyed working on this project. We learned about REST and MQTT in class, but the full extent of their usefulness did not hit me until this project. Both are incredible in terms of interoperability. Instead of writing custom components, I was able to use both to create a custom component in a fraction of the time. I plan to use MQTT to develop additional devices to implement in my house.