Online Link
Source code can be found at: https://github.com/evade-ninja/Lab5
Objective
Incorporate garage door control into the existing system while also evaluating potential security issues of adding control of a garage door via the internet.
Materials
I used the following materials:
- 1x Wemos D1 mini
- A blue LED
- 1x 330ohm resistor
- 1x Wemos Relay Shield
- 1x magnetic reed switch
- 1x breadboard
- Travel Router with VPN connection to home
- Raspberry Pi 3B+ running MQTT broker (from Lab 4)
Resources/References
I used a graphic of a garage door from The Noun Project: https://thenounproject.com/markclausnunes/uploads/?i=276226
Procedures
I started by thinking about all the different ways someone could break into my garage – both with Wi-Fi control and without.
Traditional Openers
- A nefarious individual could break into a vehicle that is parked outside and use the remote from the vehicle.
- An attacker could use a software-defined radio to capture remote control packets and replay them later. Many, but not all garage doors have switched to rolling code systems to try and combat this. That said, if enough packets are captured, it is possible that the attacker may be able to guess the next codes.
- Someone could use a sledgehammer/axe to break down the man door to the garage.
Wi-Fi Controlled Opener
- A malicious entity either has the Wi-Fi password or successfully cracks the password, accesses the controller, and opens the door.
- An internet-based hacker compromises a system on the local network, and uses that system to pivot to the controller, and opens the door.
Surprisingly, the risks from the internet are not that different from those of a traditional attack. Out of curiosity, I looked online to see how easy it would be use the SSID of a Wi-Fi access point and link it to a physical address. It turns out to be surprisingly easy. At https://wigle.net, there is a searchable database of Wi-Fi SSID’s mapped to physical locations. I was able to locate my SSID and correlate it to my physical address with surprising ease.
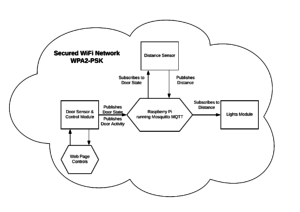
After looking at both network and physical risks and knowing that thieves are generally lazy and opportunistic, I believe that simple Wi-Fi security plus monitoring of the door status is sufficient for my needs. This however does not fit everyone’s risk profile. If one is popular online, all bets are off as nuisance attacks via the internet are more likely. In the event that someone does open the door without authorization (either physically or over the network), the door sensor will log the event and publish it to MQTT, where the alert can be acted upon. Below is a diagram of my system.
I decided to merge the control module with the door sensor module. I did this to ensure that the device controlling the door had physical access to the sensors reporting the door state. This should help protect the device against flooding the MQTT server with erroneous door state messages as it is the authoritative source of truth.
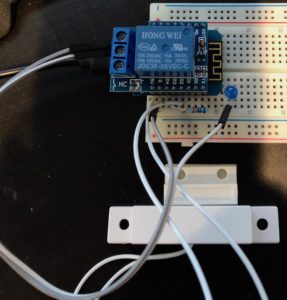
Next, I proceeded to add the relay module to the existing sensor device. I placed the relay shield on top of the Wemos D1 mini. I connected an LED with resistor through the normally open terminals of the relay, and to 5V and GND. When the relay is activated, the LED will light up to simulate connecting the door opener terminals. Below is a picture showing my device.
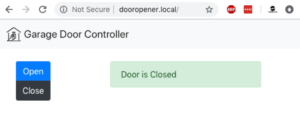
I created a simple web page as an interface to the garage door sensor/controller.
The page has two buttons, and an area to display the status of the door. The door status is refreshed every 5 seconds via an AJAX call to the device. The code for the webserver is largely repurposed from Lab 2. When the door open button is clicked, the device checks the state of the door. If the door is closed, the relay is pulsed to simulate pressing the opener button. If the door is already open, the device returns an HTTP 412 – Precondition not met. When the door close button is clicked, the device pulses the relay to close the door. It does not check the status when closing the door – in theory it is possible to open the door by clicking the close button. I did not want the door to get stuck in an unknown state and be unable to move, so I chose to have the close button ignore the current state.
Thought Questions
How did you secure devices that are not inherently secure? How does layering security help?
The Wemos devices are secured with WPA2-PSK. While this is far from a foolproof measure, it does protect against casual attacks. If I wanted to add remote access, I could add a reverse-proxy that implements authentication and SSL encryption for security.
What was your biggest challenge?
The biggest challenge was overcoming preconceptions about security. Ideally, I would consider using an ESP-32 which is capable of on-chip SSL for security.
How long did you spend on this?
Lab 2h, Report 1h